Chapter 6
Online Storage
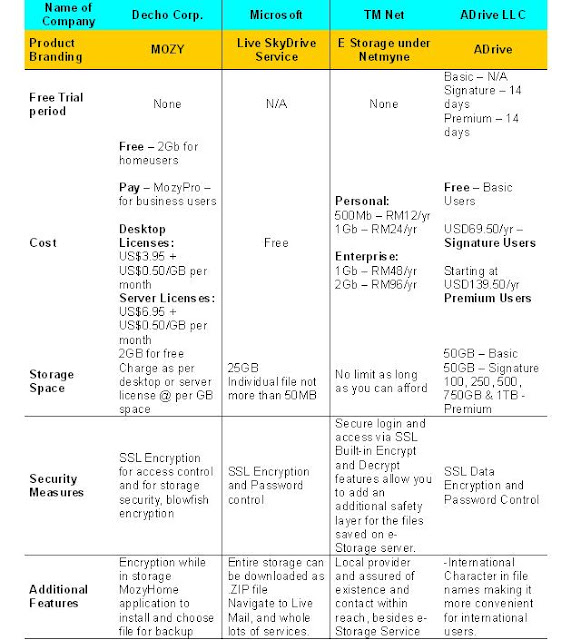
Online Storage
4 (four) different companies that provide online storage are: Decho, Microsoft, TM Net and ADrive.
Ref:
Chapter 7
Hackers
Ref:
- http://www.pcworld.com/businesscenter/article/162107/find_the_right_online_backup_service.html
- http://www.makeuseof.com/tag/windows-live-skydrive-3-alternative-storage-services/
- http://www.adrive.com/plans
- http://netmyne.com.my/osb/index.asp
- http://mozy.com/home
Chapter 7
Hackers
There are several groups of Internet users out there that will attack information systems. The three primary groups are hackers, crackers, and phreaks. While common nomenclature is to call all three of the groups “hackers,” there are some differences between the groups. There is another way of classifying types of hackers, i.e. white hat (ethical hacker), black hat (criminal hacker) and grey hat (in-between hacker). Then, there is the Script Kiddies. Thus, they can be group under 4 general types of hackers.
1. Firstly, the proper hackers are the white hat hackers. The etiquette of this type of hackers is that after they have penetrated the system, they will notify the system administrator to let the administrator know that the system has a vulnerability. It is often said that a hacker just wants security to be improved on all Internet systems.
2. The next group, the crackers, who are also the black hat hackers, are the group to really fear. These crackers have no etiquette on breaking into a system. Crackers will damage or destroy data if they are able to penetrate a system. The goal of crackers is to cause as much damage as possible to all systems on the Internet.
3. Then, we have the Script Kiddies who generally rely on previously coded scripts and pre-packaged hacking tools downloaded from the Internet to do their hacking. Script kiddies are usually individuals who are intrigued by the notion of gaining unauthorized access and are open to using untested pieces of code, especially while others (target networks and users) are at risk. Script kiddies can cause big problems against networks without truly understanding what the scripts do and what the consequences may be. This combination of irresponsible experimentation and incomplete knowledge often leads to disaster, such as the unintended loss of information.
4. The last group, phreaks, tries to break into an organization’s phone system. The phreaks can then use the free phone access to disguise the phone number from which they are calling, and also stick your organization with the bill for long-distance phone charges.
The typical profile of a hacker can be from the lone-wolf cracker seeking peer recognition to the disgruntled former employee out for revenge. A cracker’s specialty — or in some cases, his mission in life — is seeking out and exploiting vulnerabilities of an individual computer or network for their own purposes. Crackers’ intentions are normally malicious and or criminal in nature.
They usually started from the most basic of skills: software programming. The ability to write code that can control the computer is a very powerful attraction. As they gain their knowledge of operating systems, they discover the weaknesses of the OS. They also learn HTML — the code that allows them to create phony Web pages that lure unsuspecting users into revealing important financial or personal data. They can be part of a large syndicate with technical and financial support from other crackers. They have networking among themselves and exchange more and more sophisticated techniques.
In Malaysia
Among the key provisions of the ACT are:
Section 3 of Part II of the Act specified that where unauthorized access to computer material constitutes an offence under the Act. Thus, a person shall be guilty of an offence if—
(a) he causes a computer to perform any function with intent to secure access to any program or data held in any computer;
(b) the access he intends to secure is unauthorized; and
(c) he knows at the time when he causes the computer to perform the function that is the case.
And, such offence if convicted shall be liable for fine and imprisonment not exceeding fifty thousand ringgit or five years or both.
The Act also specify that unauthorized access with intent to commit or facilitate commission of further offence is punishable under Section 4, and such intention constitute an offence to be read together with the Panel Code.
Hackers do not do things for no reason unless they are some teenagers trying to gain attention. Most of the time, they do for a purpose of further gain from the availability of unauthorized information by way of selling the information or using it for further action.
Hence, it is important for the Law to govern this further benefit of unauthorised access.
The Act covers the sharing of information obtained through this way to a third party in Section 4, irrespective of the time of unauthorised access or at a future time. The fine is much severe at RM150,000 or imprisonment of 10 years or both.
Section 4 of Computer Crime Act specifies a person shall be guilty of an offence under this section if he commits an offence referred to in section 3 with intent—
(a) to commit an offence involving fraud or dishonesty or which causes injury as defined in the Penal Code [Act 574]; or
(b) to facilitate the commission of such an offence whether by himself or by any other person.
In Subsection (2), it is immaterial whether the offence to which this section applies is to be committed at the same time when the unauthorized access is secured or on any future occasion. The fine is severe to deter the person or syndicate behind the actual hacker and as mentioned in Subsection (3), fine of RM150,000 or imprisonment of 10 years can be sentenced to offenders.
The Law also made a distinction on the modification of contents under Section 5 of the Act, which many hacker would do as an attack to data integrity. Such offence is also severe at a fine of RM100,000 or imprisonment of 7 years or both.
Modification includes unauthorized modification of the contents of any computer and alteration to any particular program or data; a program or data of any kind; or a program or data held in any particular computer. Such modification is also irrespective whether permanent or merely temporary. If found guilty of an offence under this section, a fine not exceeding one hundred thousand ringgit or to imprisonment for a term not exceeding seven years can be served.
And, as cyber crimes rage over boundaries, the Computer Crime Act also incorporates the territorial scope of offences as borderless. In fact, this Law is applicable outside as well as within Malaysia
This concept of borderless jurisdiction also covers the hardware and the software, whatsoever the computer, program or data being in Malaysia or capable of being connected to or sent to or used by or with a computer in Malaysia
REF:
i. Chapter 2 – Threat to information security, INFORMATION SECURITY FUNDAMENTALS by Thomas R. Peltier, Justin Peltier & John Blackley
ii. Chapter 3 - Preventing System Intrusions by Michael West ; page 39 – 42. COMPUTER AND INFORMATION SECURITY HANDBOOK. John Vacca
iii. Law of Malaysia - Act 563, COMPUTER CRIMES ACT 1997 (Incorporating all amendments up to 1 January 2006)
iv. http://neworder.box.sk/news/4181
Chapter 8
Rivalry among PDA/smartphones
PDAs/smartphones are becoming the new craze in the world of cellular technology. After comparing the phones, write a brief paragraph stating which PDA/smartphone would best suit your needs and whether you would be willing to purchase it. Rivalry among PDA/smartphones
My choice of the smartphone would be the Nokia N97. It has neat feature of sliding and hidden keyboard, long talk time, and big storage. Its price is also less expensive than the iPhone or Samsung i8910 HD. It is not too big like the iPhone and thick enough to be of some feel. Its java enabled for web applets and can run applications like word, excel, powerpoint, PDF and video and photo editors.
Nokia is a good brand for mobile phones. My work requires frequent browsing and saving information from the Internet, therefore big storage is essentially a must. In fact, the long battery life is important as I require the phone for travelling, and sometimes, charging is not convenient at airport or train stations.
I would be purchasing it waiting for the price to come down unless Sony Ericsson comes out with similarly featured smartphone. I am a Sony Ericsson user for some time and I trust that it will have similar phone at a lower price tag.

No comments:
Post a Comment